VCDX Skill Security
Originally posted in September 2015 on vmice.net
Security skills involve knowledge regarding several categories of security. Security is just an umbrella term for so many other things because there are many ways to protect the IT infrastructure.
Since security is both a design quality and a specific component in most designs its clear that it is really important. Well it should, but most don’t pay attention to it that much. Here are some of the security categories related to IT security:
- Network Security
- Firewalls (stateful, stateless, WAF, virtual), NSX, Network segmentation (vLAN,SPAR,pVLAN etc), Access Controls, Access lists, SSL VPNs etc.
- Malware/Virus Security
- vShield Endpoint, Agent/agentless, IDS, IPS etc.
- User security
- Authentication security (LDAPs, Kerberos), organizational security policies, RBAC, DOS prevention etc.
- Data Security
- Encryption, Segmentation (Logical, Physical), Backup Copy considerations, Log keeping etc.
- Physical Security
- Datacenter access, Hardware hardening, Switch Port Security etc.
- Security Standards
- PCI-DSS, HIPAA, ISO27001:2013 etc.
- Compute Security
- Intel TXT, SGX, AES-NI, MPX, Hardware TPM, self encrypting hard drives etc.
As I mentioned earlier is security is both a design component and a design quality but it still has a lot of impact on all components of a design:
- Availability can be impacted by Denial of Service attacks, bad firmware, security flaws for root level components etc.
- Manageability can be impacted by access control, template hardening, audit software, Configuration Manager and Infrastructure Manager etc.
- Performance can be impacted by Denial of Service attacks, encryption CPU features and impact of EVC, storage isolation, network isolation etc.
- Recoverability can be impacted by data security policies, transfer protocols, backup data retention/encryption etc.
- Security can be impacted by corporate compliance to industry security standards.
For an excellent list of additional items to study on please make sure to visit Rene Van Den Bedem’s blog: http://vcdx133.com/2014/04/24/vcdx-study-plan-security/
As for all my skill updates I gathered a list of terms and technologies I wanted to learn more about and created a Quizlet.
Here are some example questions:
How is application filtering implemented?
Using Application firewalls. An application firewall is a form of firewall that controls input, output, and/or access from, to, or by an application or service. It operates by monitoring and potentially blocking the input, output, or system service calls that do not meet the configured policy of the firewall. The application firewall is typically built to control all network traffic on any OSI layer up to the application layer. It is able to control applications or services specifically, unlike a stateful network firewall, which is – without additional software – unable to control network traffic regarding a specific application. There are two primary categories of application firewalls, network-based application firewalls and host-based application firewalls.
What is an IPS?
Intrusion prevention systems (IPS), also known as intrusion detection and prevention systems (IDPS), are network security appliances that monitor network and/or system activities for malicious activity. The main functions of intrusion prevention systems are to identify malicious activity, log information about this activity, attempt to block/stop it, and report it.
What are the common compliance and government standards?
PCI-DSS for credit card data for people, HIPAA for medical records for people and Sorbanes-Oxley for financial record security.
Here is a security Deepdive slide from my VCDX slide deck that shows a graphical representation of the vSphere Security Hardening Guide.
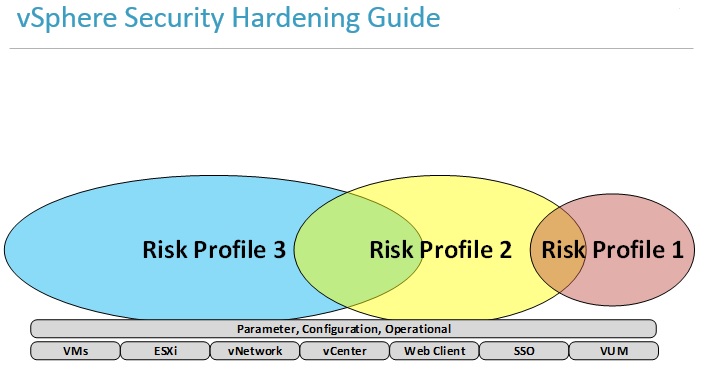
Actually the vSphere Security Hardening Guide is an excellent resource for increasing security in a vSphere environment. Many of VMware other software have a corresponding Security Hardening Guide as well.